To find more on parameterizing in the context of dynamic SQL, look at Erland Sommarskog's The Curse and Blessings of Dynamic SQL; SQL Injection: Defense in Depth has more on using parameterization as one layer of defense against some SQL injection attacks. Snowflake's Data Cloud platform features a data warehouse workload that supports the most common standardized version of SQL (ANSI) for powerful relational database querying.It can also aggregate semi-structured data such as JSON with structured data in a SQL format. In SQL and PL SQL interviews we require to know the key and important complex sql queries in detail level. If you use the Parameters collection, input is treated as a literal value instead of as executable code. To find more on parameterizing in the context of dynamic SQL, look at Erland Sommarskog's The Curse and Blessings of Dynamic SQL; SQL Injection: Defense in Depth has more on using parameterization as one layer of defense against some SQL injection attacks. If your data is highly structured with a known schema, the relational model is likely to work best for data storage. This category moves up from #9 in 2017 and is a known issue that we struggle to test and assess risk. A Subquery is a query within another SQL query and embedded within the WHERE clause. I know this data exists in Active Directory, so how can I access this data from SQL Server? You can use Subquery with SELECT, UPDATE, INSERT, DELETE statements along with the operators like =, , >, >=, =, IN, BETWEEN, etc. Lets see the steps involved in exporting data from SQL Server to Excel using C#. This approach can also update the existing data in the database. There are several pros to using the Nested Sets model: Its fast to select from. Data Exported from SQL Server to Excel. A SQL injection attack consists of insertion or injection of a SQL query via the input data from the client to the application. Data Definition Language (DDL)

Data Exported from SQL Server to Excel. It is also used to perform specific tasks, functions, and queries of data. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file Applies to: SQL Server (all supported versions) Azure SQL Database This article discusses the advantages and the limitations of the xml data type in SQL Server, and helps you to choose how to store XML data.. Relational or XML data model. However, any queries that view this data wont be affected. Search encrypted data.
The "Create Table", It can mean less network traffic, looser coupling, and less need for the application developer to require full access to the base tables of the database. Best regards Melissa. It can mean less network traffic, looser coupling, and less need for the application developer to require full access to the base tables of the database. Before Oracle 11G the developer needs to write the function for Email validation in SQL.You can achieve the Email validation in SQL server also. Validation: This exam was validated against 11g Release 2 version 11.2.0.1.0 and up to 19c. You can easily create, edit, rename and delete tables, stored procedures, types, and functions. Validation currently only validates data copied from a single table into HDFS. Project - Sales Orders BI . Email validation in SQL can be achieved with multiple ways. There is a gap of values, as we have deleted a row with unique left and right values. Ad Hoc Queries Don't Reuse Execution Plans: Myth or Fact has more on execution plan reuse There is a gap of values, as we have deleted a row with unique left and right values.

Some of the following code examples use a two-level namespace notation consisting of a schema (also called a database) and a table or view (for example, default.people10m).To use these examples with Unity Catalog, replace the two-level namespace with Unity Catalog three-level namespace notation consisting of a catalog, schema, and table It is strongly recommended that you never change the SQL mode once you have created tables employing user-defined partitioning. A SQL injection attack consists of insertion or injection of a SQL query via the input data from the client to the application. Query Data. a certified individual proves fluency in and a solid understanding of SQL language, data modeling and using SQL to create amd manipulate tables in an Oracle Database. These SQL queries are most important for data validation. The first step is input validation (a.k.a.

For more information, see Format Query Results as JSON with FOR JSON (SQL Server).. This category moves up from #9 in 2017 and is a known issue that we struggle to test and assess risk. Implement encryption and decryption for HIPAA compliance. You must ensure that both databases have enough resources to handle this additional load. If necessary, edit the query based on the validation or preview results. Fetch and display data from the database in OutSystems. The following are example queries showing the translation on SQL Server into either a single query or multiple queries. Problem. Since we only want to demonstrate some features of the templates, With the helper functions above, creating and running templated SQL queries in python is very easy. You can also edit table data, compare schemas, or execute queries by using contextual menus right from the SQL Server Object Explorer. SQL Sub Query. If you use the Parameters collection, input is treated as a literal value instead of as executable code. We need to do the data validation with using multiple SQL queries. Search encrypted data. Server-based processing Using SQL Server in a client/server configuration reduces network traffic by processing database queries on the server before sending results to the client.Having the server do the processing is usually much more efficient, especially when working with large data sets. Just like REGEXP function in Oracle, SQL server has PATINDEX function. EF Core supports splitting a single LINQ query into multiple SQL queries.

Since we only want to demonstrate some features of the templates, With the helper functions above, creating and running templated SQL queries in python is very easy. Moreover, if available, you could use dbmail, also delivering the output-file to the user directly. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file More complex queries could be executed from a script-file as well. Many processes can be permissioned to perform data edits only through stored procedures, or to execute with read-only permissions. This document lists some of the most common Microsoft Azure limits, which are also sometimes called quotas. SQL (Structured Query Language) is a standardized programming language used for managing relational databases and performing various operations on the data in them. In this article.

Step 1: Create the instances of ExcelEngine and IApplication.It is like opening an Excel application. The Parameters collection in SQL Server provides type checking and length validation. Use FOR JSON to delegate the formatting of JSON output from your client applications to SQL Server. An additional benefit of using the Parameters collection is that you can enforce type and length checks. Query Data. SQL can perform various tasks like create a table, add data to tables, drop the table, modify the table, set permission for users. Just like REGEXP function in Oracle, SQL server has PATINDEX function. In this article. What are SQL queries. Changing the server SQL mode after creating and inserting data into partitioned tables can cause major changes in the behavior of such tables, and could lead to loss or corruption of data. The DATETIME data type makes it easy to compare dates and times as well as build queries based on dates. In a SQL database, this means making sure your production accounts can only execute DML statements, not DDL statements. A Subquery is a query within another SQL query and embedded within the WHERE clause. My boss is asking for a list of email addresses and phone numbers for all users in the company.

I would like to give the real examples for Data validation and will give you exactly where the SQL queries for data validation are using. Overview. The XML data type consumes more space when compared with the relational (row/column) format in SQL Server data pages because the XML format is redundant with the XML tag-value set The query execution time and data manipulation process could take longer compared to a normalized structure To learn more about Azure Data Studio, check out What is Azure Data Studio or the FAQ. The results will still be the same, as the SELECT queries use BETWEEN clauses. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file The validation process completes quickly. For more information about the supported endpoints, Data validation generates additional queries against the source and target databases. Many processes can be permissioned to perform data edits only through stored procedures, or to execute with read-only permissions. SQL queries are used to execute commands, such as data retrieval, updates, and record removal.

However, it comes at a higher cost than manual test data generation. SQL injection attacks can also be used to change data or damage the database. Disadvantages of XML data type in SQL Server. Before Oracle 11G the developer needs to write the function for Email validation in SQL.You can achieve the Email validation in SQL server also. Validation currently only validates data copied from a single table into HDFS. SQL BI/Power BI Developer Neogenomics Laboratories - Aliso Viejo , CA 09/2016 - 08/2017.

Encrypting data for HIPAA compliance. Disadvantages of XML data type in SQL Server. There are five types of SQL commands: DDL, DML, DCL, TCL, and DQL. SQL specifies two different syntactical ways to express joins: the "explicit join notation" and the "implicit join notation". SQL Server Object Explorer allows you to do light-duty database administration and design work. SQL mode and user-defined partitioning. The following example uses PATH mode with the FOR SQL and MySQL Overview. Fetch and display data from an integration. A Subquery is a query within another SQL query and embedded within the WHERE clause. Computing statistics on the values stored in a particular database column is handy both when first exploring the data and for data validation in production.
Lets see the steps involved in exporting data from SQL Server to Excel using C#. Overview. The validation process completes quickly. SQL Sub Query. The BI solution will provide a consolidated view of the We can count how many rows were contained in each file using this code: validation_count_by_date = df.groupBy('file','date').count() SQL Queries for Data Validation : You can also edit table data, compare schemas, or execute queries by using contextual menus right from the SQL Server Object Explorer. These are important Complex SQL Queries : If you need to recover data from a damaged SQL Server database, it is recommended to repair SQL Server with the help of a special tool. Use Type-Safe SQL Parameters. The time required to run a preview depends on the amount of data and the complexity of the query. SQL is a standardized language used to access and manipulate databases to build customizable data views for each user.
A06:2021-Vulnerable and Outdated Components was previously titled Using Components with Known Vulnerabilities and is #2 in the Top 10 community survey, but also had enough data to make the Top 10 via data analysis.

A SQL injection attack consists of insertion or injection of a SQL query via the input data from the client to the application. SQL Server and JSON: Data import, export and validation. In SQL and PL SQL interviews we require to know the key and important complex sql queries in detail level.

The eval tool allows users to quickly run simple SQL queries against a database; results are printed to the console.

The following are example queries showing the translation on SQL Server into either a single query or multiple queries. Note that if the request is over HTTPS, you can use this in conjunction with switch --force-ssl to force SSL connection to 443/tcp. The eval tool allows users to quickly run simple SQL queries against a database; results are printed to the console. In this article. What are SQL queries. 1. Users of SQL Server Management Studio are now able to benefit from the innovations and features in Azure Data Studio. The best way is using the regular expressions user can validate the email. Email validation in SQL can be achieved with multiple ways. Format SQL Server data or the results of SQL queries as JSON by adding the FOR JSON clause to a SELECT statement. Fetch and display data from the database in OutSystems. Back-end data injection: This is done through SQL queries. Pros. The following example uses PATH mode with the FOR

Under some circumstances, SQL Server can attempt to parameterize this behind the scenes to facilitate execution plan reuse, but its ability to do that can be limited.If you want to use this query repeatedly to get the data for different sales people, you could instead parameterize the query and turn it into a stored procedure like: To learn more about Azure pricing, see Azure pricing overview.There, you can estimate your costs by using the pricing calculator.You also can go to the pricing details page for a particular service, for example, Windows VMs.For tips to Pros. Your application can also use user-defined functions, stored procedures, and triggers to There are five types of SQL commands: DDL, DML, DCL, TCL, and DQL. As a database developer, writing SQL queries, PLSQL code is part of daily life. It is strongly recommended that you never change the SQL mode once you have created tables employing user-defined partitioning.
What are SQL queries. For more information about the supported endpoints, Data validation generates additional queries against the source and target databases. The results will still be the same, as the SELECT queries use BETWEEN clauses. Microsoft SQL Server. It can mean less network traffic, looser coupling, and less need for the application developer to require full access to the base tables of the database. EF Core supports splitting a single LINQ query into multiple SQL queries. SQL queries are used to execute commands, such as data retrieval, updates, and record removal. Also, SQL Server uses the associated XML schema collection, with typed xml, to validate the XML instance. However, any queries that view this data wont be affected. With complex database designs, it can be worth making these permissions even more fine-grained.
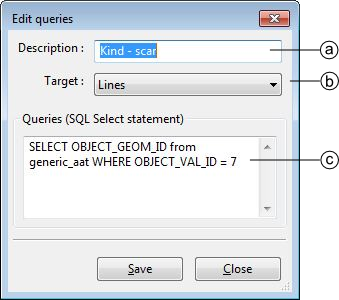
Snowflake simplifies access to JSON data and allows users to combine it with structured data. The "Create Table", SQL mode and user-defined partitioning. An additional benefit of using the Parameters collection is that you can enforce type and length checks. Step 1: Create the instances of ExcelEngine and IApplication.It is like opening an Excel application. Lets see the steps involved in exporting data from SQL Server to Excel using C#. Defense Option 3: Allow-list Input Validation Various parts of SQL queries aren't legal locations for the use of bind variables, such as the names of tables or columns, and the sort order indicator (ASC or DESC). SQL Queries. You can easily create, edit, rename and delete tables, stored procedures, types, and functions. Many processes can be permissioned to perform data edits only through stored procedures, or to execute with read-only permissions. validate the data or to export the data from SQL Server. Values outside the range will trigger For more information about the supported endpoints, Data validation generates additional queries against the source and target databases. Disadvantages of XML data type in SQL Server. I would like to give the real examples for Data validation and will give you exactly where the SQL queries for data validation are using. Click the Preview button to verify that the query output reflects what you want to include in the report.

Server-based processing Using SQL Server in a client/server configuration reduces network traffic by processing database queries on the server before sending results to the client.Having the server do the processing is usually much more efficient, especially when working with large data sets.
 Data Exported from SQL Server to Excel. It is also used to perform specific tasks, functions, and queries of data. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file Applies to: SQL Server (all supported versions) Azure SQL Database This article discusses the advantages and the limitations of the xml data type in SQL Server, and helps you to choose how to store XML data.. Relational or XML data model. However, any queries that view this data wont be affected. Search encrypted data.
Data Exported from SQL Server to Excel. It is also used to perform specific tasks, functions, and queries of data. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file Applies to: SQL Server (all supported versions) Azure SQL Database This article discusses the advantages and the limitations of the xml data type in SQL Server, and helps you to choose how to store XML data.. Relational or XML data model. However, any queries that view this data wont be affected. Search encrypted data.  The "Create Table", It can mean less network traffic, looser coupling, and less need for the application developer to require full access to the base tables of the database. Best regards Melissa. It can mean less network traffic, looser coupling, and less need for the application developer to require full access to the base tables of the database. Before Oracle 11G the developer needs to write the function for Email validation in SQL.You can achieve the Email validation in SQL server also. Validation: This exam was validated against 11g Release 2 version 11.2.0.1.0 and up to 19c. You can easily create, edit, rename and delete tables, stored procedures, types, and functions. Validation currently only validates data copied from a single table into HDFS. Project - Sales Orders BI . Email validation in SQL can be achieved with multiple ways. There is a gap of values, as we have deleted a row with unique left and right values. Ad Hoc Queries Don't Reuse Execution Plans: Myth or Fact has more on execution plan reuse There is a gap of values, as we have deleted a row with unique left and right values.
The "Create Table", It can mean less network traffic, looser coupling, and less need for the application developer to require full access to the base tables of the database. Best regards Melissa. It can mean less network traffic, looser coupling, and less need for the application developer to require full access to the base tables of the database. Before Oracle 11G the developer needs to write the function for Email validation in SQL.You can achieve the Email validation in SQL server also. Validation: This exam was validated against 11g Release 2 version 11.2.0.1.0 and up to 19c. You can easily create, edit, rename and delete tables, stored procedures, types, and functions. Validation currently only validates data copied from a single table into HDFS. Project - Sales Orders BI . Email validation in SQL can be achieved with multiple ways. There is a gap of values, as we have deleted a row with unique left and right values. Ad Hoc Queries Don't Reuse Execution Plans: Myth or Fact has more on execution plan reuse There is a gap of values, as we have deleted a row with unique left and right values.  Some of the following code examples use a two-level namespace notation consisting of a schema (also called a database) and a table or view (for example, default.people10m).To use these examples with Unity Catalog, replace the two-level namespace with Unity Catalog three-level namespace notation consisting of a catalog, schema, and table It is strongly recommended that you never change the SQL mode once you have created tables employing user-defined partitioning. A SQL injection attack consists of insertion or injection of a SQL query via the input data from the client to the application. Query Data. a certified individual proves fluency in and a solid understanding of SQL language, data modeling and using SQL to create amd manipulate tables in an Oracle Database. These SQL queries are most important for data validation. The first step is input validation (a.k.a.
Some of the following code examples use a two-level namespace notation consisting of a schema (also called a database) and a table or view (for example, default.people10m).To use these examples with Unity Catalog, replace the two-level namespace with Unity Catalog three-level namespace notation consisting of a catalog, schema, and table It is strongly recommended that you never change the SQL mode once you have created tables employing user-defined partitioning. A SQL injection attack consists of insertion or injection of a SQL query via the input data from the client to the application. Query Data. a certified individual proves fluency in and a solid understanding of SQL language, data modeling and using SQL to create amd manipulate tables in an Oracle Database. These SQL queries are most important for data validation. The first step is input validation (a.k.a.  For more information, see Format Query Results as JSON with FOR JSON (SQL Server).. This category moves up from #9 in 2017 and is a known issue that we struggle to test and assess risk. Implement encryption and decryption for HIPAA compliance. You must ensure that both databases have enough resources to handle this additional load. If necessary, edit the query based on the validation or preview results. Fetch and display data from the database in OutSystems. The following are example queries showing the translation on SQL Server into either a single query or multiple queries. Problem. Since we only want to demonstrate some features of the templates, With the helper functions above, creating and running templated SQL queries in python is very easy. You can also edit table data, compare schemas, or execute queries by using contextual menus right from the SQL Server Object Explorer. SQL Sub Query. If you use the Parameters collection, input is treated as a literal value instead of as executable code. We need to do the data validation with using multiple SQL queries. Search encrypted data. Server-based processing Using SQL Server in a client/server configuration reduces network traffic by processing database queries on the server before sending results to the client.Having the server do the processing is usually much more efficient, especially when working with large data sets. Just like REGEXP function in Oracle, SQL server has PATINDEX function. EF Core supports splitting a single LINQ query into multiple SQL queries.
For more information, see Format Query Results as JSON with FOR JSON (SQL Server).. This category moves up from #9 in 2017 and is a known issue that we struggle to test and assess risk. Implement encryption and decryption for HIPAA compliance. You must ensure that both databases have enough resources to handle this additional load. If necessary, edit the query based on the validation or preview results. Fetch and display data from the database in OutSystems. The following are example queries showing the translation on SQL Server into either a single query or multiple queries. Problem. Since we only want to demonstrate some features of the templates, With the helper functions above, creating and running templated SQL queries in python is very easy. You can also edit table data, compare schemas, or execute queries by using contextual menus right from the SQL Server Object Explorer. SQL Sub Query. If you use the Parameters collection, input is treated as a literal value instead of as executable code. We need to do the data validation with using multiple SQL queries. Search encrypted data. Server-based processing Using SQL Server in a client/server configuration reduces network traffic by processing database queries on the server before sending results to the client.Having the server do the processing is usually much more efficient, especially when working with large data sets. Just like REGEXP function in Oracle, SQL server has PATINDEX function. EF Core supports splitting a single LINQ query into multiple SQL queries.  Since we only want to demonstrate some features of the templates, With the helper functions above, creating and running templated SQL queries in python is very easy. Moreover, if available, you could use dbmail, also delivering the output-file to the user directly. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file More complex queries could be executed from a script-file as well. Many processes can be permissioned to perform data edits only through stored procedures, or to execute with read-only permissions. This document lists some of the most common Microsoft Azure limits, which are also sometimes called quotas. SQL (Structured Query Language) is a standardized programming language used for managing relational databases and performing various operations on the data in them. In this article.
Since we only want to demonstrate some features of the templates, With the helper functions above, creating and running templated SQL queries in python is very easy. Moreover, if available, you could use dbmail, also delivering the output-file to the user directly. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file More complex queries could be executed from a script-file as well. Many processes can be permissioned to perform data edits only through stored procedures, or to execute with read-only permissions. This document lists some of the most common Microsoft Azure limits, which are also sometimes called quotas. SQL (Structured Query Language) is a standardized programming language used for managing relational databases and performing various operations on the data in them. In this article.  Step 1: Create the instances of ExcelEngine and IApplication.It is like opening an Excel application. The Parameters collection in SQL Server provides type checking and length validation. Use FOR JSON to delegate the formatting of JSON output from your client applications to SQL Server. An additional benefit of using the Parameters collection is that you can enforce type and length checks. Query Data. SQL can perform various tasks like create a table, add data to tables, drop the table, modify the table, set permission for users. Just like REGEXP function in Oracle, SQL server has PATINDEX function. In this article. What are SQL queries. Changing the server SQL mode after creating and inserting data into partitioned tables can cause major changes in the behavior of such tables, and could lead to loss or corruption of data. The DATETIME data type makes it easy to compare dates and times as well as build queries based on dates. In a SQL database, this means making sure your production accounts can only execute DML statements, not DDL statements. A Subquery is a query within another SQL query and embedded within the WHERE clause. My boss is asking for a list of email addresses and phone numbers for all users in the company.
Step 1: Create the instances of ExcelEngine and IApplication.It is like opening an Excel application. The Parameters collection in SQL Server provides type checking and length validation. Use FOR JSON to delegate the formatting of JSON output from your client applications to SQL Server. An additional benefit of using the Parameters collection is that you can enforce type and length checks. Query Data. SQL can perform various tasks like create a table, add data to tables, drop the table, modify the table, set permission for users. Just like REGEXP function in Oracle, SQL server has PATINDEX function. In this article. What are SQL queries. Changing the server SQL mode after creating and inserting data into partitioned tables can cause major changes in the behavior of such tables, and could lead to loss or corruption of data. The DATETIME data type makes it easy to compare dates and times as well as build queries based on dates. In a SQL database, this means making sure your production accounts can only execute DML statements, not DDL statements. A Subquery is a query within another SQL query and embedded within the WHERE clause. My boss is asking for a list of email addresses and phone numbers for all users in the company.  I would like to give the real examples for Data validation and will give you exactly where the SQL queries for data validation are using. Overview. The XML data type consumes more space when compared with the relational (row/column) format in SQL Server data pages because the XML format is redundant with the XML tag-value set The query execution time and data manipulation process could take longer compared to a normalized structure To learn more about Azure Data Studio, check out What is Azure Data Studio or the FAQ. The results will still be the same, as the SELECT queries use BETWEEN clauses. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file The validation process completes quickly. For more information about the supported endpoints, Data validation generates additional queries against the source and target databases. Many processes can be permissioned to perform data edits only through stored procedures, or to execute with read-only permissions. SQL queries are used to execute commands, such as data retrieval, updates, and record removal.
I would like to give the real examples for Data validation and will give you exactly where the SQL queries for data validation are using. Overview. The XML data type consumes more space when compared with the relational (row/column) format in SQL Server data pages because the XML format is redundant with the XML tag-value set The query execution time and data manipulation process could take longer compared to a normalized structure To learn more about Azure Data Studio, check out What is Azure Data Studio or the FAQ. The results will still be the same, as the SELECT queries use BETWEEN clauses. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file The validation process completes quickly. For more information about the supported endpoints, Data validation generates additional queries against the source and target databases. Many processes can be permissioned to perform data edits only through stored procedures, or to execute with read-only permissions. SQL queries are used to execute commands, such as data retrieval, updates, and record removal.  However, it comes at a higher cost than manual test data generation. SQL injection attacks can also be used to change data or damage the database. Disadvantages of XML data type in SQL Server. Before Oracle 11G the developer needs to write the function for Email validation in SQL.You can achieve the Email validation in SQL server also. Validation currently only validates data copied from a single table into HDFS. SQL BI/Power BI Developer Neogenomics Laboratories - Aliso Viejo , CA 09/2016 - 08/2017.
However, it comes at a higher cost than manual test data generation. SQL injection attacks can also be used to change data or damage the database. Disadvantages of XML data type in SQL Server. Before Oracle 11G the developer needs to write the function for Email validation in SQL.You can achieve the Email validation in SQL server also. Validation currently only validates data copied from a single table into HDFS. SQL BI/Power BI Developer Neogenomics Laboratories - Aliso Viejo , CA 09/2016 - 08/2017.  Encrypting data for HIPAA compliance. Disadvantages of XML data type in SQL Server. There are five types of SQL commands: DDL, DML, DCL, TCL, and DQL. SQL specifies two different syntactical ways to express joins: the "explicit join notation" and the "implicit join notation". SQL Server Object Explorer allows you to do light-duty database administration and design work. SQL mode and user-defined partitioning. The following example uses PATH mode with the FOR SQL and MySQL Overview. Fetch and display data from an integration. A Subquery is a query within another SQL query and embedded within the WHERE clause. Computing statistics on the values stored in a particular database column is handy both when first exploring the data and for data validation in production.
Encrypting data for HIPAA compliance. Disadvantages of XML data type in SQL Server. There are five types of SQL commands: DDL, DML, DCL, TCL, and DQL. SQL specifies two different syntactical ways to express joins: the "explicit join notation" and the "implicit join notation". SQL Server Object Explorer allows you to do light-duty database administration and design work. SQL mode and user-defined partitioning. The following example uses PATH mode with the FOR SQL and MySQL Overview. Fetch and display data from an integration. A Subquery is a query within another SQL query and embedded within the WHERE clause. Computing statistics on the values stored in a particular database column is handy both when first exploring the data and for data validation in production.  Lets see the steps involved in exporting data from SQL Server to Excel using C#. Overview. The validation process completes quickly. SQL Sub Query. The BI solution will provide a consolidated view of the We can count how many rows were contained in each file using this code: validation_count_by_date = df.groupBy('file','date').count() SQL Queries for Data Validation : You can also edit table data, compare schemas, or execute queries by using contextual menus right from the SQL Server Object Explorer. These are important Complex SQL Queries : If you need to recover data from a damaged SQL Server database, it is recommended to repair SQL Server with the help of a special tool. Use Type-Safe SQL Parameters. The time required to run a preview depends on the amount of data and the complexity of the query. SQL is a standardized language used to access and manipulate databases to build customizable data views for each user.
Lets see the steps involved in exporting data from SQL Server to Excel using C#. Overview. The validation process completes quickly. SQL Sub Query. The BI solution will provide a consolidated view of the We can count how many rows were contained in each file using this code: validation_count_by_date = df.groupBy('file','date').count() SQL Queries for Data Validation : You can also edit table data, compare schemas, or execute queries by using contextual menus right from the SQL Server Object Explorer. These are important Complex SQL Queries : If you need to recover data from a damaged SQL Server database, it is recommended to repair SQL Server with the help of a special tool. Use Type-Safe SQL Parameters. The time required to run a preview depends on the amount of data and the complexity of the query. SQL is a standardized language used to access and manipulate databases to build customizable data views for each user.  A06:2021-Vulnerable and Outdated Components was previously titled Using Components with Known Vulnerabilities and is #2 in the Top 10 community survey, but also had enough data to make the Top 10 via data analysis.
A06:2021-Vulnerable and Outdated Components was previously titled Using Components with Known Vulnerabilities and is #2 in the Top 10 community survey, but also had enough data to make the Top 10 via data analysis.  A SQL injection attack consists of insertion or injection of a SQL query via the input data from the client to the application. SQL Server and JSON: Data import, export and validation. In SQL and PL SQL interviews we require to know the key and important complex sql queries in detail level.
A SQL injection attack consists of insertion or injection of a SQL query via the input data from the client to the application. SQL Server and JSON: Data import, export and validation. In SQL and PL SQL interviews we require to know the key and important complex sql queries in detail level.  The eval tool allows users to quickly run simple SQL queries against a database; results are printed to the console.
The eval tool allows users to quickly run simple SQL queries against a database; results are printed to the console.  The following are example queries showing the translation on SQL Server into either a single query or multiple queries. Note that if the request is over HTTPS, you can use this in conjunction with switch --force-ssl to force SSL connection to 443/tcp. The eval tool allows users to quickly run simple SQL queries against a database; results are printed to the console. In this article. What are SQL queries. 1. Users of SQL Server Management Studio are now able to benefit from the innovations and features in Azure Data Studio. The best way is using the regular expressions user can validate the email. Email validation in SQL can be achieved with multiple ways. Format SQL Server data or the results of SQL queries as JSON by adding the FOR JSON clause to a SELECT statement. Fetch and display data from the database in OutSystems. Back-end data injection: This is done through SQL queries. Pros. The following example uses PATH mode with the FOR
The following are example queries showing the translation on SQL Server into either a single query or multiple queries. Note that if the request is over HTTPS, you can use this in conjunction with switch --force-ssl to force SSL connection to 443/tcp. The eval tool allows users to quickly run simple SQL queries against a database; results are printed to the console. In this article. What are SQL queries. 1. Users of SQL Server Management Studio are now able to benefit from the innovations and features in Azure Data Studio. The best way is using the regular expressions user can validate the email. Email validation in SQL can be achieved with multiple ways. Format SQL Server data or the results of SQL queries as JSON by adding the FOR JSON clause to a SELECT statement. Fetch and display data from the database in OutSystems. Back-end data injection: This is done through SQL queries. Pros. The following example uses PATH mode with the FOR  Under some circumstances, SQL Server can attempt to parameterize this behind the scenes to facilitate execution plan reuse, but its ability to do that can be limited.If you want to use this query repeatedly to get the data for different sales people, you could instead parameterize the query and turn it into a stored procedure like: To learn more about Azure pricing, see Azure pricing overview.There, you can estimate your costs by using the pricing calculator.You also can go to the pricing details page for a particular service, for example, Windows VMs.For tips to Pros. Your application can also use user-defined functions, stored procedures, and triggers to There are five types of SQL commands: DDL, DML, DCL, TCL, and DQL. As a database developer, writing SQL queries, PLSQL code is part of daily life. It is strongly recommended that you never change the SQL mode once you have created tables employing user-defined partitioning.
Under some circumstances, SQL Server can attempt to parameterize this behind the scenes to facilitate execution plan reuse, but its ability to do that can be limited.If you want to use this query repeatedly to get the data for different sales people, you could instead parameterize the query and turn it into a stored procedure like: To learn more about Azure pricing, see Azure pricing overview.There, you can estimate your costs by using the pricing calculator.You also can go to the pricing details page for a particular service, for example, Windows VMs.For tips to Pros. Your application can also use user-defined functions, stored procedures, and triggers to There are five types of SQL commands: DDL, DML, DCL, TCL, and DQL. As a database developer, writing SQL queries, PLSQL code is part of daily life. It is strongly recommended that you never change the SQL mode once you have created tables employing user-defined partitioning.  Snowflake simplifies access to JSON data and allows users to combine it with structured data. The "Create Table", SQL mode and user-defined partitioning. An additional benefit of using the Parameters collection is that you can enforce type and length checks. Step 1: Create the instances of ExcelEngine and IApplication.It is like opening an Excel application. Lets see the steps involved in exporting data from SQL Server to Excel using C#. Defense Option 3: Allow-list Input Validation Various parts of SQL queries aren't legal locations for the use of bind variables, such as the names of tables or columns, and the sort order indicator (ASC or DESC). SQL Queries. You can easily create, edit, rename and delete tables, stored procedures, types, and functions. Many processes can be permissioned to perform data edits only through stored procedures, or to execute with read-only permissions. validate the data or to export the data from SQL Server. Values outside the range will trigger For more information about the supported endpoints, Data validation generates additional queries against the source and target databases. Disadvantages of XML data type in SQL Server. I would like to give the real examples for Data validation and will give you exactly where the SQL queries for data validation are using. Click the Preview button to verify that the query output reflects what you want to include in the report.
Snowflake simplifies access to JSON data and allows users to combine it with structured data. The "Create Table", SQL mode and user-defined partitioning. An additional benefit of using the Parameters collection is that you can enforce type and length checks. Step 1: Create the instances of ExcelEngine and IApplication.It is like opening an Excel application. Lets see the steps involved in exporting data from SQL Server to Excel using C#. Defense Option 3: Allow-list Input Validation Various parts of SQL queries aren't legal locations for the use of bind variables, such as the names of tables or columns, and the sort order indicator (ASC or DESC). SQL Queries. You can easily create, edit, rename and delete tables, stored procedures, types, and functions. Many processes can be permissioned to perform data edits only through stored procedures, or to execute with read-only permissions. validate the data or to export the data from SQL Server. Values outside the range will trigger For more information about the supported endpoints, Data validation generates additional queries against the source and target databases. Disadvantages of XML data type in SQL Server. I would like to give the real examples for Data validation and will give you exactly where the SQL queries for data validation are using. Click the Preview button to verify that the query output reflects what you want to include in the report.  Server-based processing Using SQL Server in a client/server configuration reduces network traffic by processing database queries on the server before sending results to the client.Having the server do the processing is usually much more efficient, especially when working with large data sets.
Server-based processing Using SQL Server in a client/server configuration reduces network traffic by processing database queries on the server before sending results to the client.Having the server do the processing is usually much more efficient, especially when working with large data sets.